Email Security is designed to protect your organisation’s e-mail from illegal access, viruses distributed by e-mail and unwanted e-mails e.g. spam. One may think of an Email Security as a firewall for your e-mail system. It functions as a filter that blocks spam messages and viruses in e-mail messages and puts suspicions content to the quarantine so you can later decide what action to take on each individual affected e-mail message.
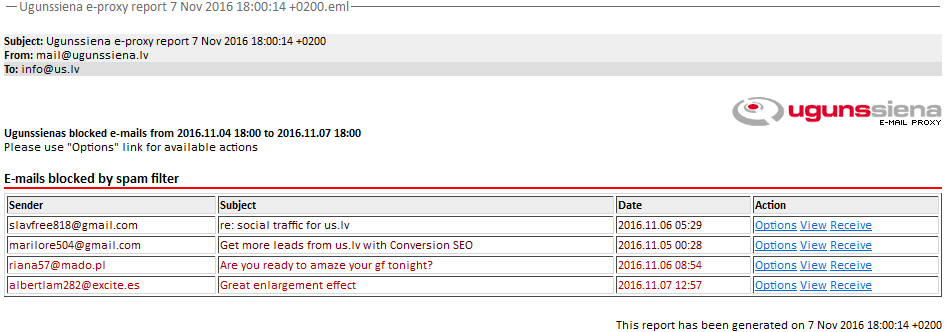
At predefined intervals of time users receive e-mail report on e-mails in quarantine e.g. blocked e-mails if any. The user then can view, delete or report as Not Spam, or receive each e-mail in quarantine.
E-mail attachment control functionality checks attachments for viruses, checks compressed attachments, blocks e-mails with attachments of forbidden type and e-mails with attachments exceeding defined size. Blocks document macros.
E-mail content control function allows blocking e-mails by the context in header and body text, wildcards allowed. Use different context rules for selected e-mail addresses or e-mail domains.
Email Security also provides Archiving functionality allowing archiving e-mail messages by e-mail address, e-mail domain name and other parameters.
Rules are used to even better control e-mail processing flow. As rules are executed in the order they appear on the list, it is possible to additionally control e-mail flow by just aligning the rules in the right order. With rules, user can set different actions to be taken on an individual e-mail address, e-mail domain name or user group. Also, user authorization can be used as a rule. When setting rule, one can use wildcards.
User groups are possible to import from AD or other LDAP server and by doing that filtering of non-existing e-mail addresses is done. To further mitigate malicious e-mail messages, domain name DNS check is done for each e-mail message. So if name address is different from one registered in DNS, e-mail is sent to quarantine.
Technical specification
E-mail filtering based on rules:
- By IP address
- By e-mail address
- By e-mail domain
- By e-mail or email domain groups defined in e-proxy
Anti-spam control:
- Combination of mathematical Artificial Intelligence methods and heuristics to eliminate spam
- Antispam control using Bayesian AI filtering methods on the actual email content
- Easily trainable by users anti-spam database with simple forwarding “Spam/Not Spam” method
- Retraining possibility when necessary
- Customer specific heuristic rules based ’email firewall’ policy
- Global, group-based and individual email-account policy granularity
- Incoming e-mail control by domain
- Outgoing e-mail control by senders e-mail address
- Control by groups using parameters mentioned above
- System-global anti-spam filters
- Dedicated anti-spam filters for selected user groups or domains
- E-mail with multiple addressees is Quarantined if contains non existing e-mail addresses
Supported protocols:
- Simple Mail Transfer Protocol (SMTP)
- SMTP authorisation
- TLS support
Compatibility with third-party e-mail systems:
- MS Exchange
- Office 365
- Lotus Notes
- SENDMAIL, Postfix and other UNIX based systems
- Novell
- Mercury
- NT e-mail servers etc.
Log and audit functions:
- Log of selected system events
- Statistical reports including virus TOP list
- Log of configuration change
- System administrator action log
E-mail attachment control functionality:
- File and attachment antivirus check
- Unpacking and inspection of compressed attachments at multiple levels
- Supporting following archive formats: zip (zipx, jar, xpi, odt, ods, docx, xlsx, epub), 7z, arj, rar, cab, and many others
- Blocking of e-mails or attachments by file type (EXE, CMD, VBS, JS, Office macro, etc.)
- Blocking of e-mails or attachments by pre-defined size
- If selected, blocking of encrypted attachments or attachments impossible to unpack (protected by password)
E-mail content control function:
- Content control by defined context in e-mail headers
- Content control by defined context in e-mail body
- Content control by defined word, phrase or template (using wildcards)
- Quarantine for filtered e-mails
- Global system-wide content control settings
- Content control for selected users or domains
Antivirus functionality:
- Antivirus control with warning messages to all parties (sender, receiver, admin)
- Antivirus control for packed or archived e-mail attachments
- Integration with various antivirus products
- Possibility to use more than one antivirus engine for all the traffic
- Automatic antivirus database update
- Quarantine for infected e-mails
Warnings about events:
- Automatic warning to sender, recipient and admin about e-mail control event like virus found, “bad” content etc.
- Warning message in pre-defined free text format
Quarantined e-mail report and search allowing to:
- Receive e-mail
- View e-mail
- Delete e-mail
- Report as Not Spam
Optimisation and settings:
- Queue control of received/to be sent messages
- Configurable number of simultaneously processed messages
- System resource control and preventive warnings if system runs low on resources
Archiving of e-mail messages:
- By address
- By domain
- By user group
- By direction of communication
Management functions:
- Web interface
- Multilanguage support with ability to switch between languages at any time
- Connection between admins console machine and e-proxy server is encrypted using SSL protocol
- Command line support
- Integrated management with management of other Ugunssiena products
- New configuration is applied to the system in real time, no restart is needed
System expansion:
- Modular design. Separate modules for e-mail security system, the antispam filter, etc. It is possible to use only a few or all of the modules available
- Selection of cryptographic algorithms for use in system according to customers needs
- Redundancy by deploying multiple hardware units
Antivirus compatibility
E-proxy works with all main antivirus vendor products. Typically we recommend using products of one of the following vendors:
- Clam AV (freeware)
- Sophos
- Kaspersky Lab
Authentication and encryption with certificate server:
- It is possible for users to set up own PKI infrastructure (generate key pairs, sign X.509 certificates and revoke them)
- Users may use system generated digital certificates for e-mail encryption


